This is an old one, but it seems it happens a lot of again.
With the installation of the IBM Sametime Video Manager gold edition (sept. 2013), the Video Manager generates an self-signed one year valid ssl certificate.
This certificate has to be trusted inside the Sametime Media System to connect via port 5061/5081 between Media Conference Bridge and Video Manager
IBM Wiki: Import the Video Manager’s certificate to the Conference Manager
After a year you get a new self-signed certificate on the Video manager and the connection between Media Conference Bridge and Video Manager ist broken (error 503). You could trust the new Video Manager certificate inside the Media Conference Bridge, but this is – again – for one year.
IBM already documented to change the certificate to a longer valid certificate or root certificate (15 years).
IBM Docu: Sametime 9 Video Manager – A/V call fails due to default root certificate expires in one year
Because of many people having problem with this documentation i will give you some more details and screenshots for this to work (from zero2hero)
- Login to the Sametime Video Manager ISC (https://yourvmgrserver:9043/ibm/console)
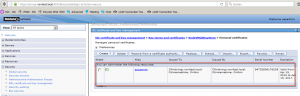
- Navigate to Security > SSL certificate & key management > key stores & certificates
- Select the option (or key store) NodeVMGRKeyStore
- Navigate to personal certificate and press the button „import certificate from a key“
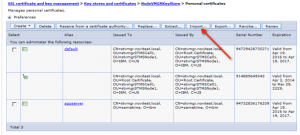
- Select the key store NodeDefaultKeyStore and enter the key store password (use „WebAS“ because it is the default password for all websphere based keystores) and press button „Get key store aliases„
- Select in the field certificate alias to import the value default and press the button OK
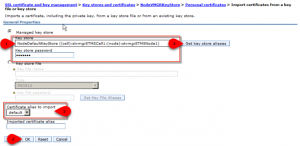
- You should now see a certificate called default with a self-signed root certificate (valid for 15years) in common.
Press SAVE to write the master configuration.
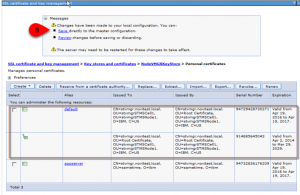
You now need to assign the new certificate to the application server
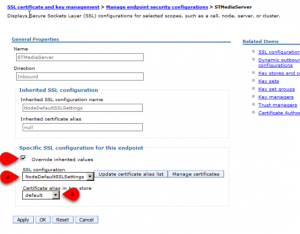
- Navigate to Security > SSL certificate & key management > Manage endpoint security configurations
- Expand the INBOUND tree until you see the application server name STMediaServer
- Klick on the servername STMediaServer
- Select „override inherited values„, select NodeDefaultSSLSetting configuration, select default certificate alias and press the button OK
Repeat this for the OUTBOUND tree until you see the application server name STMediaServer
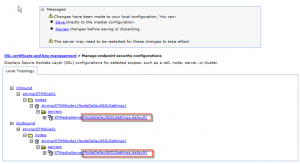
- Expand the OUTBOUND tree until you see the application server name STMediaServer
- Klick on the servername STMediaServer
- Select „override inherited values„, select NodeDefaultSSLSetting configuration, select default certificate alias and press the button OK
- Press SAVE to write the master configuration.
- Check the values in the endpoint security tree
- Restart the Sametime Video Manager in the following order
- stop STMediaServer_was.init (via service or batch)
- stop soliddb (via service or batch)
- start soliddb (via service or batch)
- WAIT 60 seconds
- start STMediaServer_was.init (via service or batch)
After this you need to import the new Video Manager certificate into the Media Conference Bridge.
- Login to the Sametime System Console ISC (https://yoursscserver:8701/ibm/console)
- Navigate to Security > SSL certificate & key management > key stores & certificates
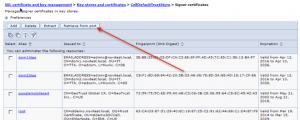
- Select the option (or key store) CellDefaultTrustStore
>> you could delete the old Video Manager certificate if you wish
- Navigate to signer certificate and press the button „retrieve from port“
- Enter the hostname for the Video Manager (e.g. myvmgrserver.dns.local) enter the port 5061 (or any other ssl port) an press the button „Retrieve signer information“
You should see now the new Video Manager root certificate – valid for 15 years
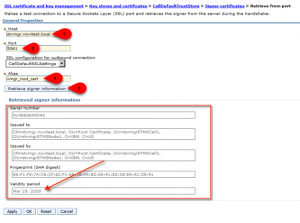
- Enter an alias name for the certificate e.g. vmgr_cert and press the button OK
- You should now see a trust certificate called vmg_cert (valid for 15years).
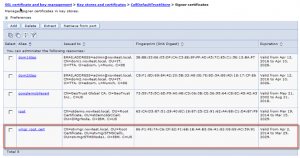
Press SAVE to write the master configuration.
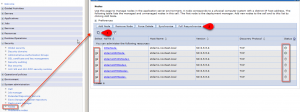
- Navigate to System administration > Nodes select all nodes and press „full synchronize“ to push the new certificate to the all applications servers
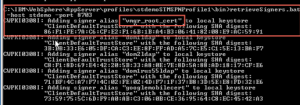
Because of having problems with the shutdown of the application server(s) after importing or changing certificates (shutdown is waiting to manually accept new certificates) i do manually retrieve the keys from the node with the following command
>> „<appserverbin>\profiles\<profilename>\bin\retrievesigners -host stsscserver -port 8703“
- Restart the Sametime Media Server (proxy registrar and/or conference bridge)
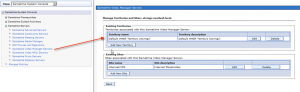
- Navigate to Sametime System Console > Sametime Servers > Sametime Video Manager Servers and check if you could connect to the Video Manager configuration
All done











